This network penetration testing guide reveals how to use penetration testing tools and best practices for conducting a penetration test.
Penetration Testing Student (PTS) is tailored for beginners. This course starts from the very basics and covers Networking & Programming skills every Pentester should have.
Understand what is penetration testing and why it is important to spend money to identify security vulnerabilities in your applications.
Learn penetration testing strategies, ethical hacking techniques to help security professionals evaluate the effectiveness of information security …


Apr 01, 2016 · Instead of simply methodology or process, PTES also provides hands-on technical guidelines for what/how to test, rationale of testing and recommended testing tools and usage. Payment Card Industry Data Security Standard (PCI DSS) Requirement 11.3 defines the penetration testing. PCI also defines


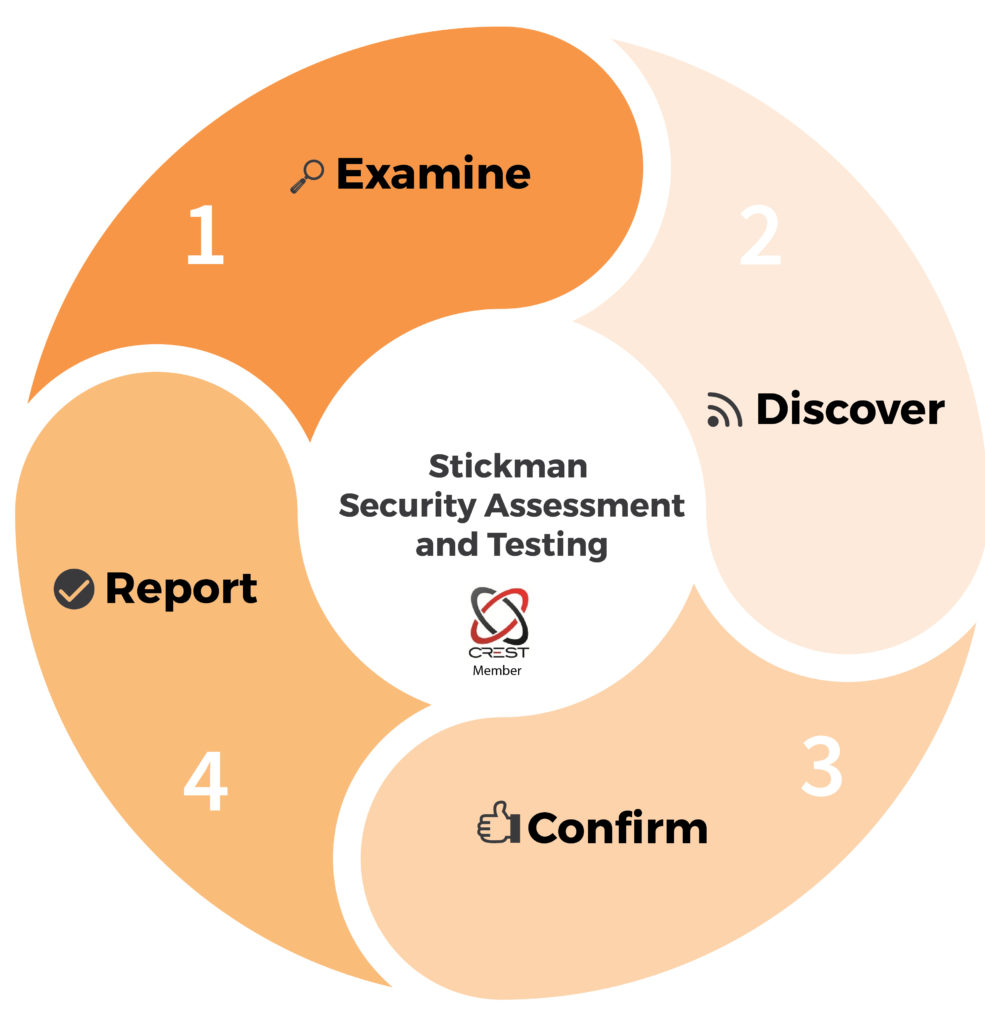



Information Supplement • The intent of this document is to provide supplemental information. Information provided here does not replace or supersede requirements in any PCI SSC Standard.
Get a real-world look at how attackers could exploit your vulnerabilities – and guidance on how to stop them – with our pen testing services.
Penetration testing (also called pen testing) is the practice of testing a computer system, network or Web application to find vulnerabilities that an attacker could exploit. The pace of application development has been increasing rapidly. Continuous testing is the only way to avoid bottlenecks
Penetration testing tools cheat sheet, a high level overview / quick reference cheat sheet for penetration testing.

Protect your business from embarrassing security failures with Corsaire’s flagship penetration testing and information security consultancy services.